What is cryptography and how to ensure the confidentiality of your information
Cryptography is a fundamental tool in the digital age, used to protect personal and business information against cyber threats. The technology is based on algorithms that transform data into a format that can only be read by those who have the decryption key. But how does it work in practice? And how do you guarantee the confidentiality of this information?
According to the survey Global Encryption Trends Study 2022, conducted by the Ponemon Institute, 72% of the organizations experienced a data breach, half of them in the previous year. At the same time, 55% of the interviewees struggle to discover where the sensitive data resides.
The Ponemon Institute also reported that 62% of the organizations have an encryption strategy in place — The biggest increase in adoption in nearly two decades:
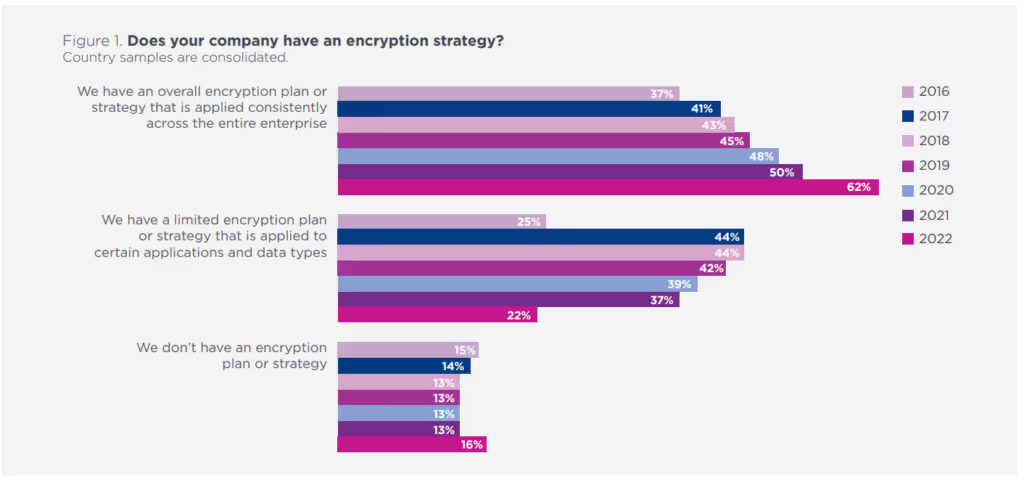
In fact, to implement a strategy capable of ensuring the confidentiality of information, it is important to choose a strong encryption algorithm and keep the decryption key in a safe place.
Additionally, it's critical to implement additional security measures, such as two-factor authentication and the use of trusted platforms.
Understanding how encryption works in practice and where it should be applied is critical to protecting your personal and business information against cyber threats. After all, as noted in the above-mentioned study, the number one barrier to the adoption of successful cryptography is the inability to find out where the organization's sensitive data is.
What is cryptography and when did it appear?
In its etymology, the word “cryptography” is derived from Greek Kryptos. The prefix “crypt-” means “hidden” or “safe” and the suffix “-graphy” means “written”.
Its origin dates back to around 2000 BC, with the Egyptian practice of hieroglyphics - complex pictograms whose full meaning was known only to a small elite to protect military and diplomatic information.

The first known modern use of this technique was made by Julius Caesar (100 BC - 44 BC), who did not trust his messengers to communicate with his governors and officers, which is why he developed a system in which each character was replaced by another three positions in front of him in the Roman alphabet.
Over the centuries, cryptography evolved to become increasingly complex and sophisticated, and with the advent of informatics, new types of algorithms and techniques emerged, providing an ever greater degree of security.
One of the most notable examples of the importance of cryptography in history was during World War II, when the Allies used cryptography to intercept and decode the Nazis' secret messages, including the Enigma code. The Allies' ability to decode German messages played a crucial role in their victory.
That said, it is clear that, currently, this has become a fundamental technology in several areas, from the protection of personal data to financial transactions, which is why it plays a crucial role in ensuring the privacy and security of information.
How does the encryption and decryption process work
Broadly speaking, the encryption process begins with the original text, which is transformed into ciphertext using a specific algorithm.
This algorithm uses the cryptographic key to mix information from the original text in a way that can only be reversed using the decryption key. The resulting encrypted message is then sent to the recipient.
To decode the message, the recipient uses this key to reverse the process of protecting that information, revealing the original message.
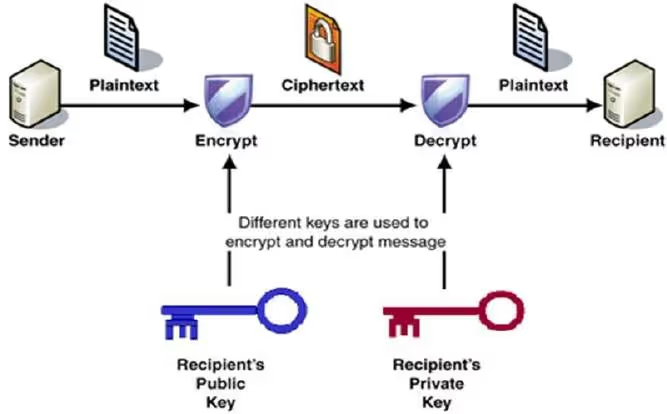
Essentially, this process can be viewed as a safe, in which the original message is placed inside and locked with a key. The key is then sent to the recipient, who uses it to open the safe and retrieve the original message.
It should be noted, however, that the encryption process does not necessarily prevent the message from being intercepted by third parties.
However, without the correct key, the encrypted message is incomprehensible, ensuring the confidentiality of the information during transmission or storage.
Importance of encryption for data protection
Encryption is important to protect data in transit (such as on a computer network) and data at rest (such as on a hard drive or flash drive). Without encryption, this data could be intercepted by hackers or other malicious individuals, which could lead to information theft, financial fraud, or a breach of privacy.
In addition, cryptography is fundamental to guarantee the authenticity of the data. Without it, it would become easy to falsify information, leading to serious consequences for companies and individuals.
That said, among its main benefits are:
- Confidentiality: Encryption helps keep information confidential, making it unreadable to anyone who doesn't have the correct decryption key. This is especially important when it comes to sensitive information, such as personal and financial data.
- Data integrity: it helps ensure that data remains intact and is not altered in an unauthorized way - especially useful when it comes to financial transactions and medical records, where data accuracy is crucial.
- Authentication: Encryption helps determine if the data obtained comes from a trusted source and was not changed during transmission.
- Regulatory compliance: ensures that companies can comply with privacy and data security regulations.
- Protection against cyber threats: Furthermore, encryption can help protect against cyber threats, such as hacker attacks and malware, since encrypted data is much more difficult for malicious people to access and decrypt.
Examples of using cryptography in practice
As seen, cryptography is an essential technique to guarantee data security and is used in various applications in our daily lives.
With that in mind, let's now explore some practical examples of how cryptography is used to protect our sensitive information.
Encryption in instant messages
Instant messaging apps, such as WhatsApp, use end-to-end encryption to ensure that conversations are secure and private. With this technology, messages are encrypted on the sender's device and can only be decrypted on the recipient's device, making it virtually impossible to intercept or read them.
Cryptography in financial transactions
Cryptography is also widely used in financial transactions, such as electronic payments and bank transactions. SSL technology (Secure Socket Layer) is an example of a mechanism used in online transactions, which protects the personal and financial information of its users.
Encryption in data storage
Data stored on devices, such as hard drives and memory cards, are other possibilities for applying this technology. For example, BitLocker, a feature integrated with Windows, allows users to encrypt the entire content of their hard drives, thus protecting their data in the event of theft or loss of the device.
Encryption in emails
Emails are another channel that may contain sensitive information that needs to be protected. At this point, encryption can and must be implemented to protect the content of the correspondence, as well as its attachments. OR PGP (Pretty Good Privacy), by way of example, is an encryption protocol used in emails to guarantee the privacy of the content.
Cloud encryption
Cryptography is also widely used in cloud storage services to protect user data against intrusions and unauthorized access.
SSL/TLS is the most common encryption protocol used to protect data transmission between cloud servers and the user's device.
Dropbox, for example, uses 256-bit Advanced Lock Key (AES) encryption to protect user files. This means that files are encrypted before being uploaded to Dropbox servers and can only be decrypted with each individual's specific encryption key.
Cryptography in electronic signatures
Encryption is essential to ensure that the electronic signature is valid and that the document is not tampered with during the shipping process.
By electronically signing a document, this technology enhances the protection of user information and the authenticity of the document in question.
In this sense, Clicksign - only Brazilian company with the ISO 27001 seal, which guarantees the highest standards of Information Security - uses high-performance cryptography, file versioning control, and various permission levels to restrict undue access to information, through Amazon Web Services (AWS) services for its infrastructure, particularly EC2 (Amazon Elastic Compute Cloud), RDS (Amazon Relational Database Service), EKS (Elastic Kubernetes Service) and S3 (Amazon Simple Storage Service).
Don't forget to take additional security measures to ensure the confidentiality of your information
Encryption is an important security measure to protect your information, but it's not the only measure you should take. By implementing additional security measures, such as strong authentication, physical security, account monitoring, and regular software updates, you can ensure the confidentiality of your information and protect yourself against security threats.
Strong authentication, it's worth remembering, is an identity verification method that requires the user to provide more than one form of authentication before accessing an account or system. This may include passwords, temporary access codes, or biometric authentication, such as fingerprints or facial recognition. Strong authentication helps prevent unauthorized third parties from accessing your information, even if the encryption is compromised.
Also, make sure that your devices are kept in safe places and that only authorized people have access to them.
Also, check your accounts frequently for suspicious activity, such as unauthorized logins or unrecognized transactions. Without a doubt, this simple attitude can help you quickly detect security issues and take steps to resolve them.
Finally, don't forget regular software updates that can help fix security vulnerabilities and keep your devices and systems even more secure.
Having said all that, don't forget: if you want to digitize your processes with all the security that technology allows, as the main companies in the market already do, in an applicable and legally valid manner, don't waste time and Try our platform now for 14 days free!
Perguntas frequentes
Resposta 1
Resposta 2
Resposta 3
Resposta 4
Resposta 5











