Types of cryptography: how they work and what is their importance
Who has never felt a touch of insecurity when including their personal data on an identification page, right? With that in mind, cryptography has become a fundamental technique to protect privacy and information security in the digital world in which we live.
After all, it works by transforming data into an indecipherable code for those who don't have the decryption key. That way, only authorized people are able to access and understand this information.
Currently, there are several types of cryptography, each with its own peculiarities and specific applications. In this post, we will explain how the main types of cryptography work, their advantages and disadvantages, and why they are so important in protecting data. If you want to know more about information security and what these codes are for in our daily lives, keep reading!
What are the main types of cryptography
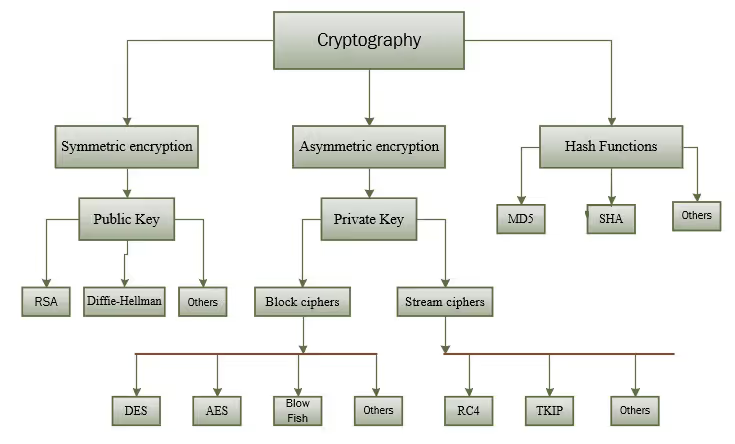
To guarantee the technique of protecting confidential information by encrypting data, making it illegible to unauthorized persons, mathematical algorithms and cryptographic keys are used, which, in their essence, can be symmetric, asymmetric or hashed.
1. Symmetric (or private key) cryptography
Symmetric cryptography is the simplest encryption technique, which uses a single key to encrypt and decrypt information.
The key is shared between authorized persons and, therefore, it is important that it be kept confidential. Its main advantage is speed, since encryption and decryption are performed quickly.
However, one point of attention is that the key can easily be compromised by an attacker, which could lead to a violation of data privacy.
Today, many email services use symmetric cryptography to guarantee the privacy of information sent by users, encrypting the message body and attachments, ensuring that only the authorized recipient can read the content of the message.
2. Asymmetric (or public key) cryptography
Asymmetric cryptography is a more advanced technique that uses two different keys to encrypt and decrypt information. One of the keys is public and can be shared with anyone, while the other key is private and must be kept private.
In this way, it becomes a more secure procedure, since the private key is extremely difficult to compromise. However, a counterpoint is its slowness, since encryption and decryption require more processing than symmetric cryptography.
In general, asymmetric cryptography is used to issue digital certificates, which are used to authenticate the identity of users in online services, such as internet banking and e-commerce. In addition, it also applies to HTTPS - a security protocol used to encrypt communication between a browser and a web server.
3. Hash encryption
Hash cryptography is a technique that produces a unique sequence of characters from a set of data.
In everyday life, it is widely used in various applications, especially in authentication and file integrity verification systems, such as electronic signature.
In an electronic signature, it is applied to the original document to generate a unique code, which is then encrypted with the signer's private key. This encrypted code, along with other information, such as the signer's digital certificate, for example, is sent along with the signed document.
Upon receiving the signed document, the recipient can verify the document's authenticity and integrity by applying the same hashing function to the original document and comparing the result with the received hash code. If the hashcodes are the same, it means that the document has not been changed and the signature is authentic.
Its main advantage is the irreversibility of the encryption process, which makes it impossible to recover the original message from the hash.
Encryption types vs. encryption codes
[caption id="attachment_16693" align="aligncenter” width="735"]
Source: Monika Agrawal, Pradeep Mishra [/caption]
If, on the one hand, the Types of cryptography are responsible for ensuring data security, on the other hand, the types of encryption code are the means by which this security is achieved.
In this sense, each code can be implemented depending on the application, the objective to be achieved and the information that will be encoded, with the objective of achieving a format that is difficult or impossible to decipher by unauthorized third parties.
These codes can be based on different principles, such as letter replacement, character permutation, binary coding, etc., among the main ones, we mention:
1. DES
Developed in the 70s, DES (Data Encryption Standard) is a type of symmetric cryptographic code that uses 56-bit keys to protect communication. Although it is an old algorithm, it is still widely used in applications such as computer networks and secure data transfer.
2. DES-X
Data, on the other hand Encryption Standard -X (DES-X), a DES variant, executes a process with a size of 184 bits and increases the difficulty of brute force access. The technique Key whitening expands the complexity of the DES-X code, making it (almost) impenetrable.
3. Triple DES
Triple DES, 3DES or 3DEA is also a DES variable and bears that name because it uses the same cryptographic pattern as the common DES, multiplied by three. Like DES-X, Triple DES works as a more secure and optimized form than the original DES. On the other hand, your total security depends on the three separate keys being turned on.
4. AES
O Advanced Encryption Standard works as cryptography and decryption, or rather, as coding and decryption. While cryptography transforms information into ciphertext, decryption takes the opposite path. The patterns of the keys used by this code vary from 128 to 256 bits.
5. RSA
RSA, or Rivest-Shamir-Adleman, is one of the first types of cryptographic codes that work publicly with secure information transmission. This is one of the codes with the highest level of security and was one of the forerunners to enable encryption in certificates and digital signatures.
6. SAFER
The SAFER encryption code (Secure And Fast Encryption Routine) can also be found as SAFER SK-64, with 64 being the standard number of bits in cryptography developed by James Massey. After its origin, new versions were designed of 40 and 128 bits.
7. Blowfish
The Blowfish encryption code is compared to the Data Encryption Standart, which, as we saw above, is a fragile brute force encryption. This cryptography has a Feistel chain with a size of 64 bit. Just as it replaces the DES code, Blowfish also works as a replacement for IDEA.
8. IDEA
With its origin in the early 90s, the International Encryption Algorithm was developed by the same creator of SAFER, James Massey. This algorithm uses blocks with keys of 128 bits and organization similar to the Data Encryption Standard encryption code.
9. Twofish
This is a derivative of Blowfish and the difference is that the number of keys in this code reaches up to 256 bits. But what exactly does that number mean? In short, the quantity reveals how fast Twofish works. Another evolution comes in sequence, the Threefish, reaching no more, no less, than 1024 bits.
10. Camellia
Camellia is a Modern Feistel cipher similar to AES and, like the previous code, it operates with blocks of 128, 192, and 256, as well as 18 rounds or 24 rounds. In addition to being a modern cipher, Camellia is on this list because of its high level of security. Not even brute force is able to enter the system.
How encryption is used to ensure the security of your online data
In a more simplified way, cryptography is a network of mathematical algorithms that encode personal information that only the users and recipients themselves can access. This prevents the data from being defrauded and allows us to enter our identification without the possibility of access by others.
In practice, cryptography acts together with the activities of technological security to ensure our routine activities on the internet. In addition to accessing bank accounts, non-encryption means allowing others to access even the most intimate information, such as home addresses.
Luckily, progress is guaranteed and we can currently do it online shopping and electronic signatures without our identification being ceaselessly leaked.
That said, now that you know what the main types of codes and encryption are, don't forget to prioritize information security in your business.
Finally, remember that Clicksign is the only Brazilian company in the electronic signature market with ISO 27001 certification, ensuring the highest standard of cyber protection!
We have adopted procedures to encrypt Information stored in Amazon S3 with the AES-256 cipher algorithm. Thus, the Clicksign databases are encrypted and the encryption is programmed to take place in S3, before the Information is saved.
In addition, Clicksign uses Transport Layer Security (TLS) minimum version 1.2 with extended validation and 256-bit encryption to increase the protection of Information during transmission over public networks.
TLS is a security protocol that guarantees data integrity between two communication applications. It aims to ensure that the connection between the browser, apps, and web services is secure and reliable.
Thus, Clicksign performs tests to confirm the adequate functioning of the Platform in the current versions of the market-leading browsers.
Therefore, if you want to know more about how Online Document Signing can revolutionize your processes and enhance the legal validity of your data, take a free test and see how it is possible to formalize a contract in less than 1 minute. Try it, no credit card required!











