What is ISO 27001? Understanding the Information Security Standard
Information Security it is an area that has been gaining more and more attention on the companies' agenda in recent years. In this sense, knowing what ISO 27001 is becomes fundamental in a scenario in which cyber threats emerge increasingly sophisticated and affecting organizations of all sizes and branches of activity.
Monday to McKinsey, the damage caused by cyberattacks will be around $10.5 trillion a year by 2025 — one 300% increase compared to 2015 levels.
In this sense, ISO (International Organization for Standardization), an institution founded in 1946 and based in Geneva, Switzerland, has the mission of promoting the development of standards, tests and certification with the highest standard in various areas of activity.

Therefore, in this article, we will discuss the importance of ISO 27001 certification for companies and the main strategies to guarantee its validation, providing a robust framework to protect confidential information and reduce the risk of breaches on the internet.
What is ISO 27001?
The ISO/IEC 27001 standard- Information Technology - Security Techniques - Information Security Management Systems - Requirements (commonly known as ISO 27001), published in October 2005 by International Organization for Standardization And hair International Electrotechnical Commission, is an international standard that provides guidelines for information security management.
The purpose of this certification is to establish a set of requirements to help organizations establish and manage an information security management system (ISMS), capable of disseminating guidelines for identifying, evaluating, and treating imminent risks in the area.
In addition, it provides a systematic approach to managing such risks and allows companies to comply with legal and regulatory assumptions related to data protection. According to the ISO 27001 Global Report:
“ISO 27001 is one of the most popular cybersecurity standards in the world, with certifications growing more than 450% in the last ten years.”
According to document According to the basic guidelines of the OECD (Organization for Economic Cooperation and Development), there are 9 principles of Information Security (awareness, responsibility, response, risk analysis/assessment, security architecture and implementation, security management and reassessment, ethics and democracy), ISO 27001 with its ISMS implements 7 of them.
What are the ISO 27001 requirements?
To obtain ISO 27001 certification, it is necessary to align your Information Security Management Systems with the requirements of the standard. These requirements aim to help organizations create, maintain, and continuously improve their ISMS posture.
There are seven requirements of ISO 27001, listed in clauses 4-10 of the compliance framework, with which your organization must become compatible, these are:
Requirement 1 - Context of the organization (clause 4)
Before defining your scope for implementing the ISMS, it is essential to know your company. This is a crucial part, as it will inform stakeholders, including managers, C-levels, clients, investors, auditors, and employees, which areas of your company will be covered by your planning.
The auditor also uses this scope during the ISO 27001 Audit to understand the risks for which you identified and implemented measures of security within the organization.
Requirement 2 - Leadership and Commitment (Clause 5)
The organization's top leadership must demonstrate ownership and commitment to certification, participating in training programs and providing the teams involved with the necessary resources to carry out their work efficiently.
Requirement 3 - Planning for risk management (clause 6)
ISO 27001 does not determine an exhaustive list of measures for companies to implement. Instead, the standard requires organizations to adapt unique and customized security measures and policies to the reality of their business.
Requirement 4 - Resource Allocation (Clause 7)
Here, companies are required to allocate the necessary resources to meet the requirements to obtain and manage this seal, as well as to assume the commitment that the functions, responsibilities, and authorities are clearly defined.
Requirement 5 - Evaluations of operational controls (clause 8)
ISO 27001 requires organizations to continuously monitor their ISMS and assess whether the performance of the controls and policies implemented is effective. With periodic performance evaluations, companies are expected to improve their systems to consistently meet requirements.
In addition, these performance evaluations must be documented and presented as evidence during an audit to demonstrate compliance.
Requirement 6 - Performance Assessment (Clause 9)
Institutions must carry out several internal audits to monitor, measure, analyze, and evaluate their ISMS.
These audits must ensure that the information security management system meets business goals and objectives, as well as the requirements of ISO 27001, being reviewed at the accreditation stage by an independent external auditor.
Requirement 7 - Plan for improvement and correction of non-compliances (clause 10)
In general terms, whenever there is a non-compliance in your ISMS, your organization must document this setback, with reasons that explain what caused the occurrence and what corrective measures will be implemented.
In addition to the seven requirements mentioned above, ISO 27001 also includes annexes to assist in the implementation of the SGSI. The annexes include information on risk analysis, security controls, compliance assessment, SGSI audit, personnel training, and documentation.
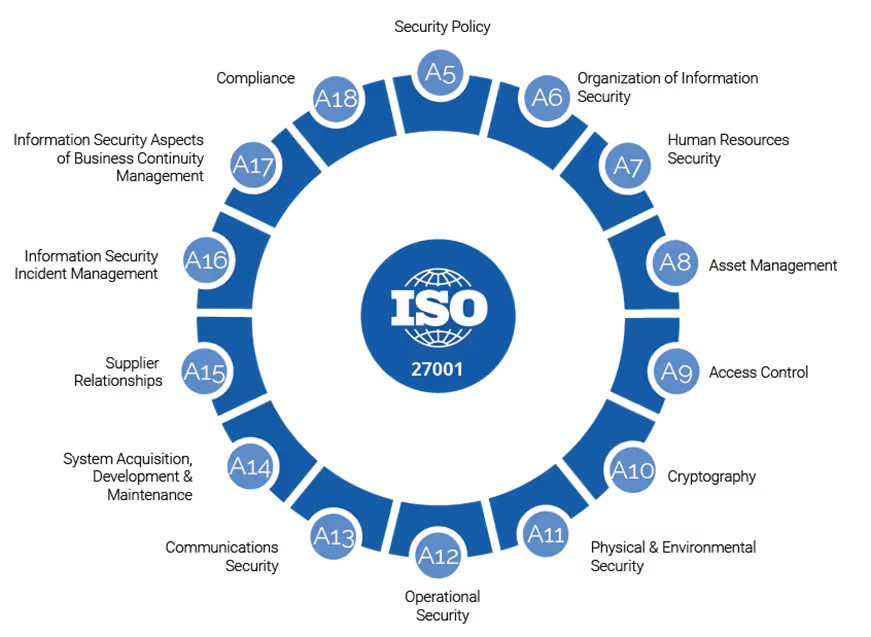
Step by step to implement the standard
Implementing the ISO 27001 standard can be a challenge for many institutions, however, this is a valuable initiative that can help ensure data protection and the trust of customers and end users in your company.
In this sense, to conquer the seal and obtain the statuses for the preservation of information, some fundamental steps are:
- Start with an implementation team: form a dedicated team to implement the standard and include representatives from all areas of the company, including IT, human resources, and the legal department.
- Understand the scope of ISO 27001: the second step includes identifying the information system that will be covered by the standard and determining which processes and activities will be included. This is because it is important to remember that it is not a universal solution for all your company's information security issues and that it is necessary to clearly define the scope to obtain the best results.
- Conduct a risk analysis: the next step is to identify and assess the vulnerability and potential impact of these risks. For this, it is crucial to take into account all sources of threat, including internal threats, such as human error, and external threats, such as cyber intrusions. It should be noted that this step must be repeated continuously as the environment changes and threats evolve.
- Define the security measures capable of mitigating them: after identifying risks, the next step is to define security measures to manage those risks. They must be appropriate and proportionate to the risks identified and include not only the implementation of technical but also administrative security controls. Additionally, it's important to consider financial, legal, and compliance implications when selecting available alternatives.
- Implement security measures and access controls: the next step is to implement clearly defined security measures, such as configuring hardware and software, deploying policies and procedures, including encryption, user authentication, backup, and disaster recovery, and conducting training to ensure understanding and compliance with security measures. Also, configure your systems to control access to sensitive data. This includes restrictions on access to systems, applications, and data.
- Continuously monitor and evaluate: finally, it's important to continuously monitor and evaluate security measures to ensure they're working as planned and to identify any necessary changes.
- Contingency plan: develop contingency plans to ensure business continuity in the event of an interruption.
In addition to these requirements, companies must also involve all employees in the implementation of ISO 27001 so that they understand how their role can help protect the organization's sensitive information.
Remember that the implementation of the ISO 27001 standard is an ongoing process and must be updated regularly to ensure that information security is always up to date and protected.
Benefits of ISO 27001 and why is it important?
As seen, the implementation of this standard brings many benefits to companies and is an effective way to ensure that your company is prepared to deal with threats to information security, among these main advantages, we mention:
- Sensitive Information Protection: ISO 27001 helps ensure that sensitive company information is protected against leaks, security intrusions, and other threats. This is important as sensitive information can be used to harm the company or its customers.
- Regulatory compliance: many regulations, including General Data Protection Law (LGPD) in Brazil, they require companies to implement measures to protect their customers' sensitive information. ISO 27001 helps companies to comply with these regulations.
- Reputation Improvement: companies that implement ISO 27001 can increase their credibility and reputation in the market by showing their customers and suppliers that they are committed to information security.
- Risk Management: ISO 27001 is based on a risk management approach that helps companies identify, assess, and mitigate information security risks. This is important because it helps prevent future security issues.
- Customer Protection: the protection of sensitive customer information is crucial to their trust and loyalty to the company.
Clicksign is the only Brazilian company in the electronic signature market with this certification

At Clicksign, security is a serious thing. Therefore, among the many initiatives that guarantee the data protection of your documents, Achievement of ISO 27001 was a milestone in the sector.
Currently, We are the only Player 100% Brazilian market share electronic signature to obtain such a certificate valid in the national territory.
Clicksign's implementation of ISO 27001 demonstrates its commitment to protecting the information security of its customers.
This means that the company follows strict safety standards and undergoes independent audits to verify compliance with the standard.
As you can see, Clicksign is the ideal solution to accelerate the growth and preservation of your business! Therefore, if you want to know more about how Online Document Signing can revolutionize your processes, click here and talk to an expert.






.jpg)




